|
Size: 3083
Comment:
|
Size: 4513
Comment:
|
| Deletions are marked like this. | Additions are marked like this. |
| Line 1: | Line 1: |
| = More Firewall rules and VNC access to your Kali Linux = | = Lab 03 - More Firewall rules and Remote access to your VMs = |
| Line 5: | Line 5: |
| 1. First we are going to setup your Kali linux to allow SSH and VNC - your final goal is to show a VNC login from your Windows 10 Box. | 1. Setup rdp backdoors to your windows machines on pfsense using NAT 1. Setup ssh keys on github and use them to access your ubuntu, and kali machines. Again, setup backdoors using NAT 1. Setup xrdp for kali (that way you can access it without having to use the SCVMM tool. |
| Line 7: | Line 9: |
| 1. Explore the metasploitable box and see what ports are open on it. This will involve a bit of work relating to nmap. Goal is to list all open ports and the common programs that run on those ports. |
|
| Line 16: | Line 16: |
| 1. Install the openssh-server on kali (you know how, I shouldn't have to tell you) 1. Make sure the service always starts on a reboot (ditto here, hint update-rc.d) |
1. Install the openssh-server on kali (you know how, I shouldn't have to tell you), it should already be install on your ubuntu server. 1. Create a public key private key pair and post your public key on git hub (see: https://help.github.com/articles/connecting-to-github-with-ssh/. Once you have your public key posted on github others can access it via: "github.com/username.keys" YOu can use that to your advantage when installing the keys. I used wget to get the keys from github. 1. Make sure the open ssh service always starts on a reboot of kali (ditto here, hint update-rc.d) |
| Line 20: | Line 21: |
| 1. Now you should be able to login from your Windows 10 machine (using putty, did you install that yet?) and sudo su|bash or whatever you want to use to become root! And you don't ever need that crazy IE for this either. 1. Now that you are root, why not take this opportunity to update|upgrade your system. 1. This is not as easy as it may sound. You should know to do a apt-get update, apt-get upgrade, apt-get dist-upgrade, and now full-upgrade. BUT THIS MAY NOT WORK HERE! Why? Because you are installing software that will set off all sorts of alarms in most security suites. |
1. Now you should be able to login from your Windows 10 machine (using bitvise, did you install that yet?) and sudo su|bash or whatever you want to use to become root! And you don't ever need that crazy IE for this either. 1. Now that you are root, take this opportunity to update|upgrade your systems. 1. This is not as easy as it may sound for kali. You should know to do a apt-get update, apt-get upgrade, apt-get dist-upgrade, and now full-upgrade. BUT THIS MAY NOT WORK HERE! Why? Because you are installing software that will set off all sorts of alarms in most security suites. So you may have trouble with your kali update. |
| Line 26: | Line 27: |
| 1. Update all machines except metasploitable 3. | 1. Update all machines except metasploitable 3. * Hint if you your having trouble with pfSense, try the following: 1. Check the networking 2. Login to pfSense and do an upgrade from the commandline. # sudo pfSense-upgrade -d |
| Line 28: | Line 32: |
| 1. Install xrdp on kali (I'm assuming your ubuntu does not have a gui). 1. Install NAT rules to allow you to ssh into your linux machines and rdp into your windows machines. You can use any port you like to forward to your internal machines (which should all have static IPs of course) |
|
| Line 29: | Line 35: |
| 1. Finally, I want to have a remote desktop ability to Kali 2. (e.g. RDP+VNC). However there seems to be problems with VNC and Gnome 3. 1. I had to remove Gnome 3 and install mate. [[https://alancads.wordpress.com/2016/05/10/remove-gnome-3-and-install-mate-kali-linux-rolling-edition/|With directions here.]] 1. You can change to and from booting to terminal with the following commands: * To switch from GUI to CLI: {{{systemctl set-default multi-user.target}}} * To switch from CLI to GUI: {{{systemctl set-default graphical.target}}} 1. You can change which GUI you are using with: {{{update-alternatives --config x-session-manager}}} |
=== Show me === |
| Line 36: | Line 37: |
| In-Progress! | 1. Show me that you can login to each of the following machines from the lab network and that you have installed all updates except on Metasploitable 3! 1. Windows 10 1. Window Server 1. Kali 1. Ubuntu 18.04 1. Show me that you can login to kali via ssh and rdp. 1. Show me that you can rdp into your windows 10 machines directly from outside your firewall (yes these is a back door) 1. Show me that you can ssh into your linux machines using bitvise and a public key from outside your firewall (yes these are back doors) |
| Line 38: | Line 46: |
| 1. Let's install the "vino" vnc server. (Follow your favorite [[http://xmodulo.com/how-to-set-up-vnc-server-on-linux.html|tutorial]] 1. I also had to install dconf-editor |
= 2019 Examle screen shots = == Showing Ubuntu == Here is an example of what I did for my ubuntu. First I setup a reserved IP for the ubuntu system. {{attachment:screen3.png}} Then I setup a NAT rule and firewall rule to allow port 2222 to be forwarded to my ubuntu machine on port 22. {{attachment:screen2.png}} Then I can login from an ubuntu prompt on my system at home: {{attachment:screen1.png}} == Showing for Windows == I installed Windows 2019 server (not the desktop experience version). From powershell, I had to do several things - see WindowsAdministration/PowerShellScripts#Setting_up_a_Windows_2019_Server_for_the_first_time When you are done, it should show the following: {{attachment:screen4.png}} You could do this for both windows systems if you like. |
Lab 03 - More Firewall rules and Remote access to your VMs
Goal
- Setup rdp backdoors to your windows machines on pfsense using NAT
- Setup ssh keys on github and use them to access your ubuntu, and kali machines. Again, setup backdoors using NAT
- Setup xrdp for kali (that way you can access it without having to use the SCVMM tool.
Understand Firewall rules and how they are processed on pfSense
Lab Guide
There will be a lecture and demo of firewall rules.
First we are going to setup
- Install the openssh-server on kali (you know how, I shouldn't have to tell you), it should already be install on your ubuntu server.
Create a public key private key pair and post your public key on git hub (see: https://help.github.com/articles/connecting-to-github-with-ssh/. Once you have your public key posted on github others can access it via: "github.com/username.keys" YOu can use that to your advantage when installing the keys. I used wget to get the keys from github.
- Make sure the open ssh service always starts on a reboot of kali (ditto here, hint update-rc.d)
- Can you login over ssh with root? Ok, then add yourself
- Don't forget to add yourself to the right group (hint: usermod will do that for you).
- Now you should be able to login from your Windows 10 machine (using bitvise, did you install that yet?) and sudo su|bash or whatever you want to use to become root! And you don't ever need that crazy IE for this either.
- Now that you are root, take this opportunity to update|upgrade your systems.
- This is not as easy as it may sound for kali. You should know to do a apt-get update, apt-get upgrade, apt-get dist-upgrade, and now full-upgrade. BUT THIS MAY NOT WORK HERE! Why? Because you are installing software that will set off all sorts of alarms in most security suites. So you may have trouble with your kali update.
- Solution? I had to use a SOCKS proxy to end around this. You all should collaborate to see if you can find a solution. I've given you a hint, here is another. There are only a couple of .deb files that will fail so you could just download them through another means (again, the means I used was a SOCKS proxy).
- Make sure you have updated your Windows 10, and Windows 2016 machines too.
- Since the most important step in security is to make sure your machines are up-to-date...
- Update all machines except metasploitable 3.
- Hint if you your having trouble with pfSense, try the following:
- Check the networking
- Login to pfSense and do an upgrade from the commandline. # sudo pfSense-upgrade -d
- Hint if you your having trouble with pfSense, try the following:
- Make sure that all machines will continue to update on a regular bases.
- Update all machines except metasploitable 3.
- Install xrdp on kali (I'm assuming your ubuntu does not have a gui).
- Install NAT rules to allow you to ssh into your linux machines and rdp into your windows machines. You can use any port you like to forward to your internal machines (which should all have static IPs of course)
Show me
- Show me that you can login to each of the following machines from the lab network and that you have installed all updates except on Metasploitable 3!
- Windows 10
- Window Server
- Kali
- Ubuntu 18.04
- Show me that you can login to kali via ssh and rdp.
- Show me that you can rdp into your windows 10 machines directly from outside your firewall (yes these is a back door)
- Show me that you can ssh into your linux machines using bitvise and a public key from outside your firewall (yes these are back doors)
2019 Examle screen shots
Showing Ubuntu
Here is an example of what I did for my ubuntu. First I setup a reserved IP for the ubuntu system.
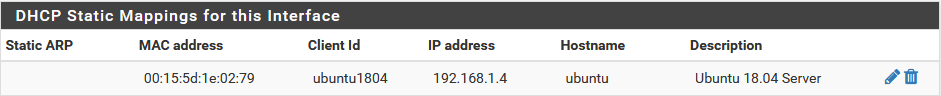
Then I setup a NAT rule and firewall rule to allow port 2222 to be forwarded to my ubuntu machine on port 22.
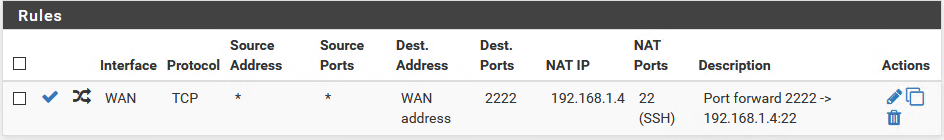
Then I can login from an ubuntu prompt on my system at home:
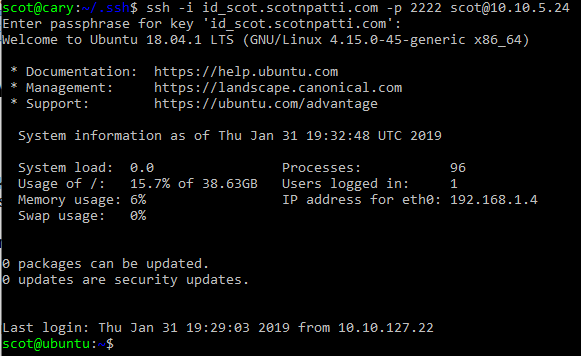
Showing for Windows
I installed Windows 2019 server (not the desktop experience version).
From powershell, I had to do several things - see WindowsAdministration/PowerShellScripts#Setting_up_a_Windows_2019_Server_for_the_first_time
When you are done, it should show the following:
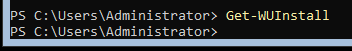
You could do this for both windows systems if you like.
