|
Size: 1372
Comment:
|
Size: 1405
Comment:
|
| Deletions are marked like this. | Additions are marked like this. |
| Line 23: | Line 23: |
| 1. '''Security Attacks'''. An example can be seen here: {{attachment:OSI Model.png}} | 1. '''Security Attacks'''. An example can be seen here: {{attachment:OSI 1. 1. {{attachment:OSI Model.png}} |
Describe NetworkSecurityEssentials4
This page includes Dr. A's own notes on Network Security Essentials 4th Edition.
Chapter 1
- No clear boundary exists between computer security and network/Internet security. This book comes to the problem from the network security side.
- CIA triad from "computer security"
Confidentiality
Integrity
Availability
- Many experts add:
- Authenticity
- Accountability (non-repudiation, deterrence, fault isolation, intrusion detection and prevention, after-action recovery and legal action)
- Computer security is complex
- Requirements stated in one word, but mechanisms to fulfill requirements often complex
- Security mechanisms prone to attack
- Threat analysis to a security service may reveal additional complexity
- Placement of the mechanisms not trivial... see the rest on page 8.
- OSI securiity model
Users and software use Security Services which in turn use...
Security Mechanisms to block
Security Attacks. An example can be seen here: {{attachment:OSI 1.
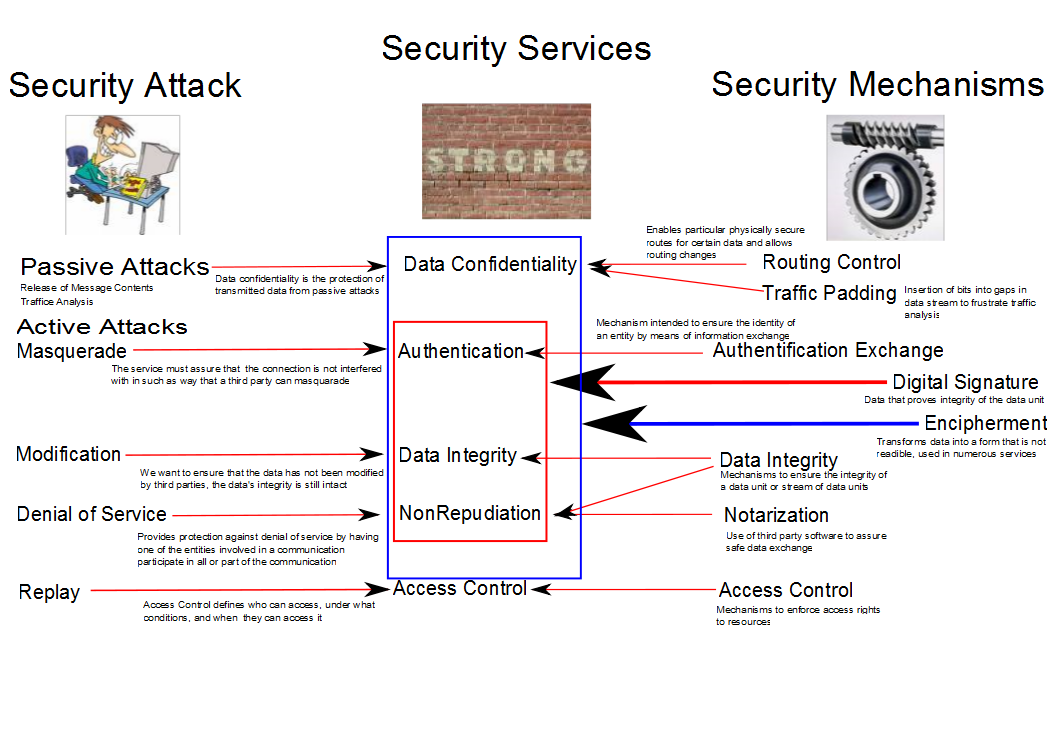
- You should know these categories well!
