|
Size: 1661
Comment:
|
Size: 3374
Comment:
|
| Deletions are marked like this. | Additions are marked like this. |
| Line 1: | Line 1: |
| = Describe NetworkSecurityEssentials4 = | = NetworkSecurityEssentials4 Notes Not From Lectures = |
| Line 23: | Line 23: |
---- /!\ '''Edit conflict - other version:''' ---- 1. '''Security Attacks'''. An example can be seen here: {{attachment:OSI Model.png}} |
1. '''Security Attacks'''. An example can be seen in Figure 1. 1. Figure 1. {{attachment:OSI Model.png}} |
| Line 28: | Line 27: |
| ---- /!\ '''Edit conflict - your version:''' ---- 1. '''Security Attacks'''. See the Figure below. 1. {{attachment:OSI Model.png}} 1. You should know these categories well! |
== Chapter 13 == |
| Line 33: | Line 29: |
| ---- /!\ '''End of edit conflict''' ---- | 1. What is cybercrime? The department of justice categorizes cybercrimes into three categories: 1. Computers as targets: This form of crime targets a computer system, to acquire information stored on that computer system, to control the target system without authorization or payment (theft of service), or to alter the integrity of data or interfere with the availability of the computer or server. Using the terminology of Chapter 1, this form of crime involves an attack on data integrity, system integrity, data confidentiality, privacy, or availability. 1. Computers as storage devices: Computers can be used to further unlawful activity by using a computer or a computer device as a passive storage medium. For example, the computer can be used to store stolen password lists, credit card or calling card numbers, proprietary corporate information, pornographic image files, or “warez” (pirated commercial software). 1. Computers as communications tools: Many of the crimes falling within this category are simply traditional crimes that are committed online. Examples include the illegal sale of prescription drugs, controlled substances, alcohol, and guns; fraud; gambling; and child pornography. 1. Intellectual Property (Patents and Copyright issues) 1. What is a patent, what does it cover, how long is it in place for? 1. What is a copyright, what does it cover, how long is it in place for? 1. In your opinion, which of these is the most abused by the owners? Which is the most abused by the users? 1. Privacy (We discussed this on the first day of class) 1. What privacy protections are in place in the USA? How do these differ from other countries? (Especially European) 1. Be able to name some of the relevant laws regarding privacy in the USA. Be able to describe at least one of them in detail. 1. Material I prepared on Privacy (2010) [[attachment:Privacy, Legal and Ethical Issues.pptx]] 1. Ethics 1. Professional Ethics {{attachment:ethics.bmp}} 1. [[attachment:COE_Flyer.pdf|ACM Code of Ethics]] |
NetworkSecurityEssentials4 Notes Not From Lectures
This page includes Dr. A's own notes on Network Security Essentials 4th Edition.
Chapter 1
- No clear boundary exists between computer security and network/Internet security. This book comes to the problem from the network security side.
- CIA triad from "computer security"
Confidentiality
Integrity
Availability
- Many experts add:
- Authenticity
- Accountability (non-repudiation, deterrence, fault isolation, intrusion detection and prevention, after-action recovery and legal action)
- Computer security is complex
- Requirements stated in one word, but mechanisms to fulfill requirements often complex
- Security mechanisms prone to attack
- Threat analysis to a security service may reveal additional complexity
- Placement of the mechanisms not trivial... see the rest on page 8.
- OSI securiity model
Users and software use Security Services which in turn use...
Security Mechanisms to block
Security Attacks. An example can be seen in Figure 1.
Figure 1.
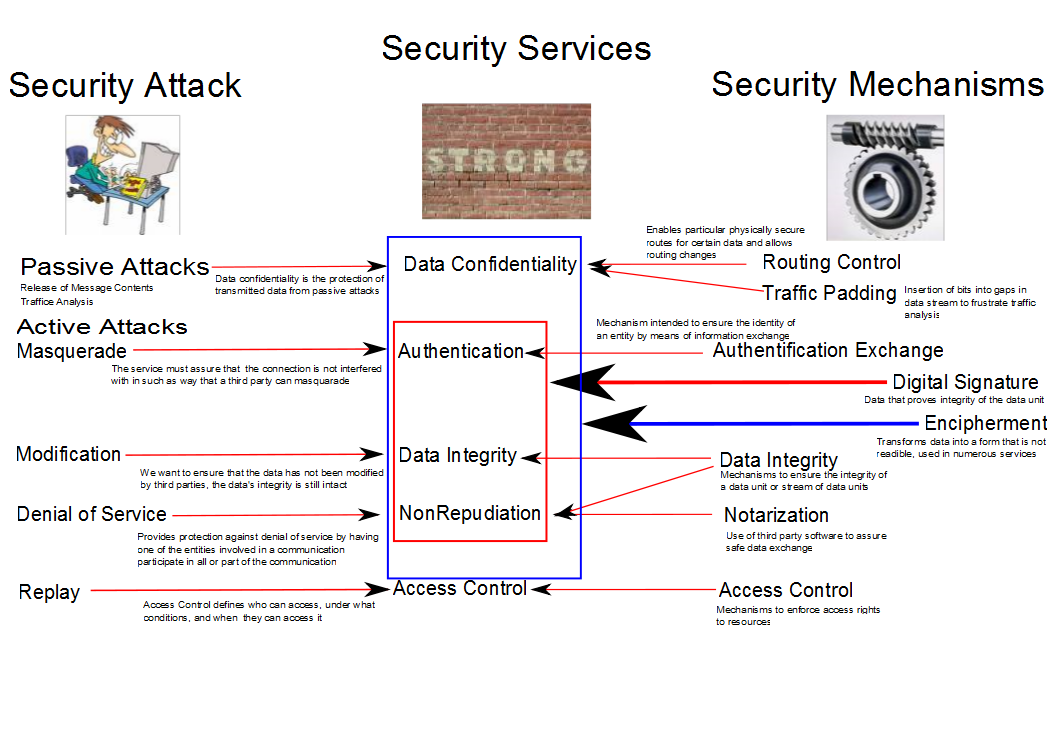
- You should know these categories well!
Chapter 13
- What is cybercrime? The department of justice categorizes cybercrimes into three categories:
- Computers as targets: This form of crime targets a computer system, to acquire information stored on that computer system, to control the target system without authorization or payment (theft of service), or to alter the integrity of data or interfere with the availability of the computer or server. Using the terminology of Chapter 1, this form of crime involves an attack on data integrity, system integrity, data confidentiality, privacy, or availability.
- Computers as storage devices: Computers can be used to further unlawful activity by using a computer or a computer device as a passive storage medium. For example, the computer can be used to store stolen password lists, credit card or calling card numbers, proprietary corporate information, pornographic image files, or “warez” (pirated commercial software).
- Computers as communications tools: Many of the crimes falling within this category are simply traditional crimes that are committed online. Examples include the illegal sale of prescription drugs, controlled substances, alcohol, and guns; fraud; gambling; and child pornography.
- Intellectual Property (Patents and Copyright issues)
- What is a patent, what does it cover, how long is it in place for?
- What is a copyright, what does it cover, how long is it in place for?
- In your opinion, which of these is the most abused by the owners? Which is the most abused by the users?
- Privacy (We discussed this on the first day of class)
- What privacy protections are in place in the USA? How do these differ from other countries? (Especially European)
- Be able to name some of the relevant laws regarding privacy in the USA. Be able to describe at least one of them in detail.
Material I prepared on Privacy (2010) Privacy, Legal and Ethical Issues.pptx
- Ethics
Professional Ethics
